Steps to use a pointbase database provided with Weblogic Installation :
- Copy ” pbembedded.lic ” located in ” C:\bea10.3\wlserver_10.3\common\eval\pointbase\lib ” to ” C:\bea10.3\wlserver_10.3\common\eval\pointbase\tools “
- We need to create two security database – one for the source side domain and another for the destination end domain.
- Now start the PointBase server ( run ” startPointBase.cmd ” located in ” C:\bea10.3\wlserver_10.3\common\eval\pointbase\tools “
- Start the PointBase console ( run ” startPointBaseConsole.cmd ” located in ” C:\bea10.3\wlserver_10.3\common\eval\pointbase\tools “
- Login using the user name ” EXAMPLES ” and password ” EXAMPLES “

- Now lets create a database table using the sample ” rdbms_security_store_pointbase.sql ” located in ” C:\bea10.3\wlserver_10.3\server\lib “

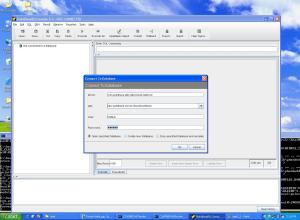
So now we have successfully created two security database, lets cerate the domains now.
We need to create the following domains on WLS 10.3.x :
Domain1 name : saml_source ; non ssl port : 7001 ; ssl port : 7002
Domain2 name : saml_destination ; non ssl port : 7003 ; ssl port : 7004
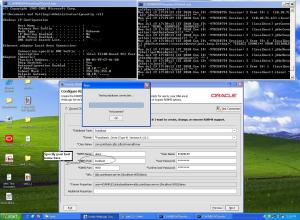
Now run the ” Configuration Wizard ” On the ” Customize Environment and Services Settings ” screen select the option ” Yes “

- Select the option “I want to create, change, or remove RDBMS support” and make the changes as shown in the figure below, and also click on ” Test Connection ” button to make sure that the database is configured properly.
- We need to configure ” Custom Identity and Custom Trust ” on Weblogic servers.
Link : http://wls4mscratch.wordpress.com/2010/06/08/steps-to-configure-custom-identity-custom-trust-on-wls/
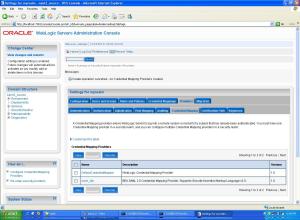
- Now we need to configure ” Credential Mapper ” on the IDP end.
- So to ” myrealm ” –> ” Providers ” –> ” Credential Mapping ” –> and add a ” SAML2CredentialMapper ” as shown below :

- Now click on the newly created SAML2CredentialMapper say ” saml_IDP ” and make the following changes :
- Issuer URI : http://www.souresite.com/saml
- Name Qualifier : sourcesite.com
- Web Service Assertion Signing Key Alias : cooldragon
- Web Service Assertion Signing Key Pass Phrase : **********
- Please type again To confirm : *********

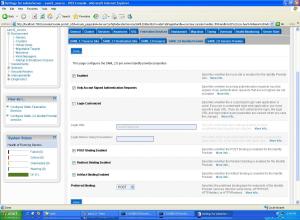
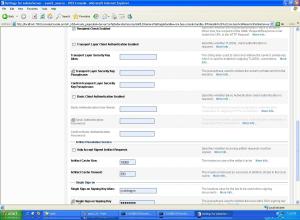
- Click on ” Servers ” –> Admin Server –> ” Federation Services ” –> ” SAML 2.0 Identity Provider ” and make the following changes :
- Enabled : check
- Only Accept Signed Authentication Request : check
- Preferred Binding : POST
- Now click on ” Servers ” –> Admin Server –> ” Federation Services ” –> ” SAML 2.0 General ” and make the following changes :
- Replicated Cache Enabled – Uncheck
- Contact Person Given Name
- Contact Person Surname
- Contact Person Type
- Contact Person Company
- Contact Person Telephone Number
- Contact Person Email Address
- Organization Name
- Organization URL
- Published Site URL : http://
: /saml2 - Entity ID : ( Source Domain name)
- Single Sign-on Signing Key Alias
- Single Sign-on Signing Key Pass Phrase
- Confirm Single Sign-on Signing Key Pass Phrase
- Save the changes and export the IDP metadata into a XML file –> Click on “ Publish Meta Data ” button. ( say IDP_Metadata.xml ). We need to copy this file to the destination domain later.


————–
Destination Side :
Now we need to generate the SAML destination site ( SP ) metadata
- Click on ” myrealm ” –> ” Providers ” –> ” Authentication ” –> new ” SAML2IdentityAsserter “

- Click on ” Servers ” –> Admin Server –> ” Federation Services ” –> ” SAML 2.0 Service Provider ” and make the following changes :
- Enabled : check
- Always Sign Authentication Requests : check
- Force Authentication : Check
- Preferred Binding : POST
- Default URL : http://
: /samldest01App

- Now click on ” Servers ” –> Admin Server –> ” Federation Services ” –> ” SAML 2.0 General ” and make the following changes :
- Replicated Cache Enabled : Uncheck
- Contact Person Given Name
- Contact Person Surname
- Contact Person Type
- Contact Person Company
- Contact Person Telephone Number
- Contact Person Email Address
- Organization Name
- Organization URL
- Published Site URL : http://
: /saml2 - Entity ID : ( Destination Domain name)
- Single Sign-on Signing Key Alias
- Single Sign-on Signing Key Pass Phrase
- Confirm Single Sign-on Signing Key Pass Phrase

More Here
Courtesy:http://wls4mscratch.wordpress.com/2010/07/22/steps-to-configure-saml-2-on-weblogic-server-10-3-x/