Firstly, you'll need a private key. Note that it is the private key which is used for signing. The public key (usually contained within an X.509 public key certificate) is used for the signature validation, and can be inserted into the XML Signature block, but it is the private key which is used for the actual signing. Here is a link to information about how to create a public and private key pair in Vordel SOAPbox or the Vordel Policy Studio. You can also, of course, import a private key (or a certificate and private key pair) as a PKCS#12 file. Or, in the case of the Vordel appliance with the HSM (Hardware Security Module), you can point your configuration to the private key, and the private key never leaves the hardware.
Once you have your private key available to you, you can then configure an XML Signature Generation filter (which is found in the "Integrity" group in Policy Studio). Note that it is also available under the "Design Mode" of the free SOAPbox tool, when you create a test case (under "Workspace" create a "test suite" and then create a "test case").
The XML Signature Generation filter should go after a filter which inserts a SAML Assertion. Here is a description of how to insert a SAML assertion containing attributes into a SOAP message.
Choose your signing key by clicking on the "Signing Key" button below. As you can see, it shows "(unset)" until you set it.
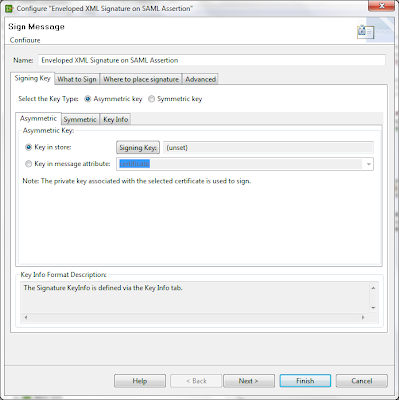
Under the "What to sign" tab, choose the XPath sub-tab and select the first SAML 2.0 assertion option.
In "Where to place signature", chose the option "

 SAML Subject (Before) (SAML 2.0)". This means that an enveloped signature is created, meaning that the signature is placed inside the SAML assertion itself. This means that if the SAML assertion is taken from the message and placed into another message, it is still valid.
SAML Subject (Before) (SAML 2.0)". This means that an enveloped signature is created, meaning that the signature is placed inside the SAML assertion itself. This means that if the SAML assertion is taken from the message and placed into another message, it is still valid.When we test this with a message sent from the free SOAPbox Web Services testing tool , we see the signed SAML assertion returned. The issuer information ("Vordel") is configurable. Notice that, because the XML Signature is "enveloped", it is contained within the SAML assertion block itself.
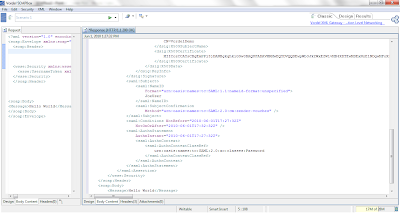
If we scroll down the response in SOAPbox, we see the contents of the SAML assertion which we've signed. This includes details of the user ("JoeUser") who was authenticated, and the method of authentication (password).
More Here
Courtesy:http://www.soatothecloud.com/2010/06/signing-saml-assertion.html